Passwordless Login Explained: Benefits and Best Practices

Did you know that password-related attacks cause 81% of data breaches worldwide? Traditional logins seem familiar, but they leave digital doors wide open to hackers and headaches for users. As technology advances, organizations and individuals are searching for safer and simpler ways to prove identity online. Exploring passwordless login reveals a promising shift toward smoother, more secure access while exposing common myths and real-world challenges.
Key Takeaways
| Point | Details |
|---|---|
| Enhanced Security | Passwordless authentication significantly reduces vulnerabilities associated with traditional passwords, using advanced verification methods like biometrics and cryptography. |
| Implementation Complexity | Transitioning to passwordless systems requires careful planning and substantial investment in infrastructure and user training. |
| User Experience Improvement | By eliminating complex password requirements, passwordless login enhances user interaction and reduces frustrations related to password resets. |
| Potential Drawbacks | Organizations must address challenges such as device compatibility and privacy concerns to successfully implement passwordless solutions. |
Defining Passwordless Login and Common Myths
Passwordless login represents a transformative approach to digital authentication that eliminates traditional password requirements. Passwordless authentication allows users to access systems and applications without manually entering complex passwords, instead leveraging alternative verification methods like registered devices, biometrics, or cryptographic tokens.
According to research from Wikipedia, this method fundamentally improves security by removing several critical vulnerabilities associated with password-based systems. Key advantages include:
- Enhanced security through device-based or biometric verification
- Reduced risk of credential theft
- Elimination of password-related support costs
- Simplified user experience
- Better tracking and visibility of authentication events
However, academic research highlights some nuanced challenges with passwordless approaches. As detailed in a recent academic study, passkeys – a popular passwordless method – come with specific limitations. These include device-binding complexities and potential issues around account recovery and multi-device synchronization.
Common myths about passwordless login often misrepresent its capabilities. While incredibly promising, it’s not a universal, plug-and-play solution. Organizations must carefully evaluate implementation strategies, understanding that passwordless authentication requires thoughtful integration, user education, and robust backup authentication mechanisms. The goal isn’t just eliminating passwords, but creating a more secure, user-friendly authentication ecosystem.
Primary Methods of Passwordless Authentication
Passwordless authentication offers multiple innovative approaches to secure digital access, each leveraging unique technologies to replace traditional password-based login mechanisms. Among these methods, passkeys and biometric authentication stand out as leading solutions transforming how users verify their digital identities.
According to Wired, passkeys represent a cutting-edge authentication method using public-private key cryptography. In this approach, a public key is stored by the service provider, while the private key remains securely stored on the user’s device, protected by biometrics or a PIN. Key characteristics of passkeys include:
- Multi-factor authentication without additional user friction
- Phishing-resistant design
- Growing support across major operating systems and browsers
- Enhanced security through cryptographic verification
Research from an academic study highlights the significant advantages of passkey technology over traditional authentication methods. Compared to Time-Based One-Time Passwords (TOTP), passkeys offer superior security and improved usability. As detailed in the academic research, these methods effectively address multiple security threats, including:
- Phishing attempts
- Password leak vulnerabilities
- Brute-force attack risks
Beyond passkeys, other passwordless authentication methods include biometric verification (fingerprint, facial recognition), hardware tokens, and push notifications to registered devices. Each method offers unique benefits, allowing organizations to select an approach that best balances security, user experience, and technical infrastructure requirements.
Security Advantages Over Traditional Passwords
Passwordless authentication represents a quantum leap in digital security, addressing fundamental vulnerabilities inherent in traditional password-based systems. By eliminating shared secrets and leveraging advanced cryptographic techniques, this approach offers unprecedented protection against modern cybersecurity threats.
According to research from Clerk, FIDO2-based passwordless authentication demonstrates extraordinary security capabilities. The data reveals a staggering 99% phishing resistance compared to traditional password methods. This dramatic improvement stems from public-key cryptography, which prevents credential compromise during potential server breaches.
Key security advantages include:
- Complete elimination of password-related attack vectors
- Prevention of credential stuffing and password reuse
- Zero storage of shareable authentication secrets
- Device-specific cryptographic verification
- Reduced risk of social engineering attacks
As highlighted by Duo, passwordless authentication aligns perfectly with zero trust security models. By removing passwords—historically the primary target for cybercriminals—these methods fundamentally transform authentication mechanisms. The technology prevents critical vulnerabilities like:
- Multi-factor authentication (MFA) fatigue
- Prompt bombing
- Phishing attempts
- Credential harvesting
Ultimately, passwordless authentication isn’t just an incremental improvement—it’s a revolutionary approach that rebuilds authentication from the ground up, prioritizing user experience without compromising robust security standards.
Implementation Requirements for Organizations
Passwordless authentication represents a significant technological transformation that demands careful strategic planning and substantial organizational commitment. While the benefits are compelling, successful implementation requires a comprehensive approach addressing technical, cultural, and financial considerations.
According to research from Clerk, organizations should anticipate substantial initial investments. Typical implementation costs range between $300,000-$450,000, spanning 6-8 months and requiring 25-30 full-time equivalent work months. However, the long-term financial outlook is promising, with operational costs potentially dropping 40-80% in support and security incident management.
Key implementation requirements include:
- Comprehensive technology infrastructure assessment
- Robust identity management systems
- Cross-departmental collaboration
- User training and change management programs
- Compatibility testing across existing software platforms
Technical considerations are critical during passwordless authentication deployment. Organizations must carefully evaluate:
- Device and browser compatibility
- Integration with existing security frameworks
- Multi-factor authentication strategies
- Backup authentication mechanisms
- Compliance with industry-specific regulatory requirements
Academic research from implementation-focused studies emphasizes designing systems that balance security, usability, and performance. The goal isn’t just technological replacement, but creating a seamless, secure authentication ecosystem that enhances both user experience and organizational protection. Strategic planning, phased rollout, and continuous monitoring will be essential to successfully transition from traditional password systems to modern passwordless authentication approaches.

Comparing Passwordless and Conventional Logins
Passwordless authentication fundamentally reimagines digital security by addressing critical vulnerabilities inherent in traditional login methods. Unlike conventional password-based systems that rely on memorized secrets, passwordless approaches leverage advanced cryptographic technologies to create a more secure, user-friendly authentication experience.
Research from Clerk reveals remarkable performance advantages in security metrics. Passwordless systems demonstrate near-perfect protection against common attack vectors:
- Phishing Resistance: Nearly 100% effectiveness
- Credential Stuffing: Virtually impossible to execute
- Computational Efficiency: WebAuthn signature verification requires less processing power than traditional password hashing
Key comparative differences include:
-
Authentication Mechanism
- Conventional: Shared secret (password)
- Passwordless: Device-specific cryptographic tokens
-
User Experience
- Conventional: Complex password creation, frequent resets
- Passwordless: Seamless, friction-free access
According to Duo, passwordless authentication eliminates multiple pain points associated with traditional logins. The practical benefits extend beyond security, dramatically improving user interaction by removing:
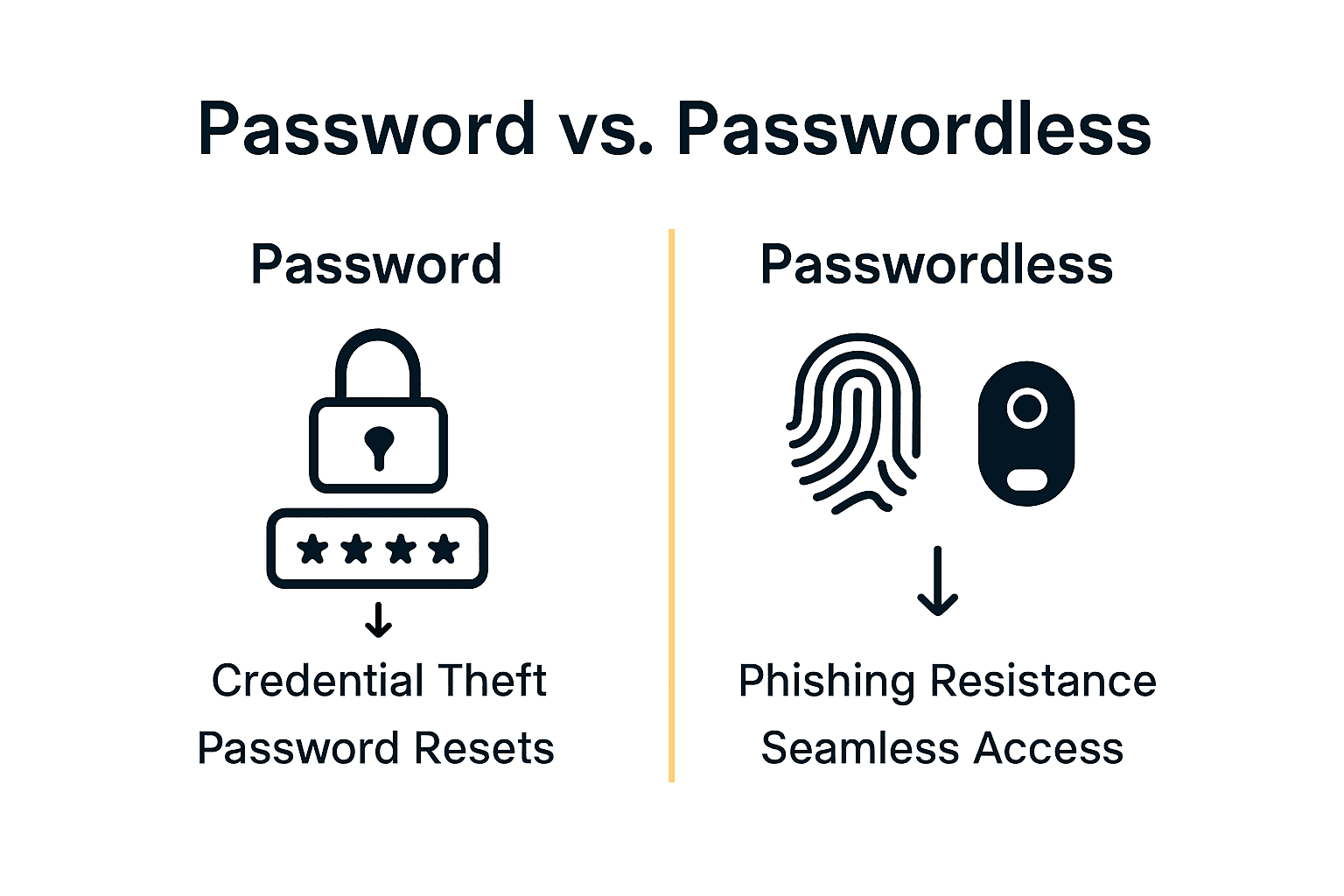
- Password reset frustrations
- Multi-factor authentication prompt fatigue
- Risk of credential theft
Ultimately, passwordless authentication represents more than a technological upgrade—it’s a comprehensive reimagining of digital identity verification that prioritizes both robust security and exceptional user experience.
Here’s a side-by-side summary of passwordless vs. traditional authentication:
| Aspect | Traditional Passwords | Passwordless Authentication |
|---|---|---|
| Authentication Method | User-created password | Device cryptography Biometrics Tokens |
| Security Risks | Credential theft Phishing Password reuse |
Phishing-resistant No password reuse Device-bound |
| User Experience | Frequent resets Complex rules |
Seamless Fewer interruptions |
| Cost Over Time | High support costs | Lower long-term support |
| Implementation Complexity | Simple initial setup | Higher upfront investment |
| Recovery & Backup | Password reset processes | Backup authentication methods needed |
Addressing Potential Drawbacks and Risks
Passwordless authentication, while revolutionary, is not without its challenges. Organizations must carefully navigate potential risks and limitations to ensure successful implementation and maintain robust security standards.
According to analysis from Portnox, several critical drawbacks demand strategic consideration:
- Limited device compatibility with older hardware
- Privacy concerns surrounding biometric data collection
- Higher upfront implementation costs
- Complex setup and management processes
- Potential single points of failure if devices are compromised
The comprehensive cybersecurity perspective from Payoda further illuminates potential risks that organizations must proactively address. Key vulnerability areas include:
- Biometric spoofing techniques
- Token theft possibilities
- Excessive device dependency
- Integration challenges with legacy systems
- Privacy regulation compliance complexities
Mitigating these risks requires a multifaceted approach. Organizations should:
- Implement robust device validation mechanisms
- Develop comprehensive backup authentication strategies
- Create clear user education programs
- Maintain flexible authentication pathways
- Continuously monitor and update security protocols
While passwordless authentication introduces innovative security improvements, it is not a universal solution. Successful implementation demands nuanced understanding, strategic planning, and ongoing adaptation to emerging technological and security landscapes.
Make Passwordless Login a Reality With LogMeOnce
Still facing the stress and security risks of managing passwords every day? The article above uncovers how passwordless authentication cuts out password fatigue while defending your business from phishing and cyber threats. With the rising need for frictionless logins, multi-factor authentication, and secure cloud access, organizations require a trusted solution that transforms these best practices into real-world results.
See the difference for yourself. Discover how LogMeOnce delivers advanced passwordless MFA, easy single sign-on, secure encrypted storage, and continuous dark web monitoring in one seamless platform. Start your journey to stronger cybersecurity and a smoother user experience now by exploring our identity management solutions. Join businesses and agencies worldwide who chose easier, safer authentication—because protecting your digital life cannot wait.
Frequently Asked Questions
What is passwordless login?
Passwordless login is an authentication method that allows users to access systems and applications without entering traditional passwords, using alternatives like biometrics, device verification, or cryptographic tokens instead.
What are the benefits of using passwordless authentication?
Passwordless authentication enhances security by eliminating vulnerabilities associated with passwords, reduces the risk of credential theft, lowers support costs, simplifies the user experience, and improves tracking of authentication events.
Are there any drawbacks to passwordless authentication?
Yes, potential drawbacks include limited device compatibility, privacy concerns related to biometric data collection, higher upfront implementation costs, and reliance on specific devices, which can create single points of failure if compromised.
How does passwordless authentication compare to traditional login methods?
Passwordless authentication offers superior security by using device-bound cryptographic tokens instead of shared passwords, significantly reduces phishing risks, and provides a frictionless user experience compared to the complexities of password management like resets and rule compliance.





 Password Manager
Password Manager
 Identity Theft Protection
Identity Theft Protection

 Team / Business
Team / Business
 Enterprise
Enterprise
 MSP
MSP



