In the ever-evolving landscape of cybersecurity, the recent leak of passwords has raised significant concerns among users and experts alike. These leaked credentials, often found in data breaches from popular platforms and shared on dark web forums, highlight the vulnerabilities that can arise from poor password management and security practices. The significance of these leaks lies not only in the immediate risk of unauthorized access to personal accounts but also in the broader implications for online safety, urging users to adopt stronger, unique passwords and consider implementing solutions like Single Sign-On (SSO) to safeguard their digital identities. As we delve into the world of SSO, understanding the impact of leaked passwords serves as a crucial reminder of the importance of robust cybersecurity measures.
Key Highlights
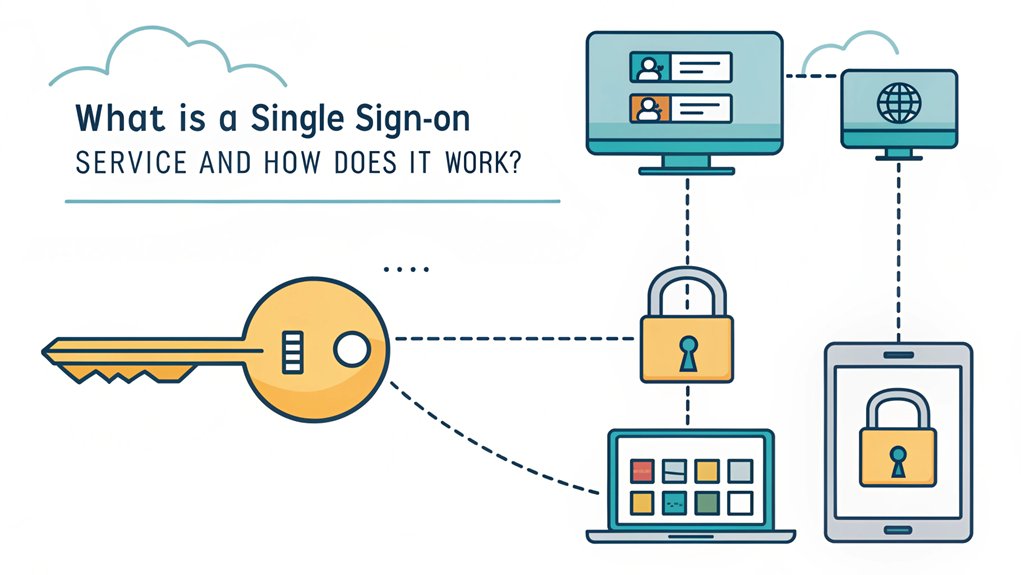
- Single Sign-On (SSO) is an authentication system that lets users access multiple applications with one set of login credentials.
- SSO creates secure tokens that verify user identity across different services, eliminating the need for multiple passwords.
- When users log in through SSO, an Identity Provider verifies credentials and communicates with Service Providers to grant access.
- Users only need to authenticate once, and the SSO system automatically logs them into other connected applications.
- SSO enhances security by reducing password management complexity while allowing centralized control over user access permissions.
Understanding Single Sign-On: The Basics
Imagine having a magical key that opens all your favorite doors at once! That's exactly what Single Sign-On (SSO) does for your computer. I like to think of it as a super-smart password that works everywhere.
You know how you need different passwords for your games, school websites, and other fun stuff? Well, SSO lets you use just one password to gain access to them all! It's like having a special bracelet that tells every door, "Hey, I know this person – let them in!"
When you type in your SSO password, it creates a special ticket (we call it a token) that tells other websites, "This is my friend – they're allowed to play here!" Isn't that cool? This makes everything safer because having one strong password reduces the chances of bad guys getting into your accounts.
No more remembering lots of different passwords or asking Mom and Dad for help!
Key Benefits of SSO Implementation
SSO is like having a magical master key for all your digital treasures! Just imagine not having to remember tons of different passwords – it's like having one super-special key that opens all your favorite games and apps.
| Awesome Benefits | What It Means | Why It's Cool |
|---|---|---|
| Super Easy | One password for everything | No more forgetting passwords! |
| Extra Safe | Better protection for your stuff | Like having a superhero guard |
| Money Saver | Less time fixing password problems | More time for fun things |
You know how frustrating it is when you can't remember your password for your favorite game? With SSO, that's history! Companies love it too – they save over $1 million yearly in password resets. Isn't that amazing? Plus, it's getting so popular that by 2027, it'll be worth $2.2 billion – that's like filling two swimming pools with money! The system uses identity providers to securely verify who you are across all your apps, which enhances security by minimizing password fatigue and potential breaches.
The Technical Architecture Behind SSO
Three super-important friends work together to make SSO work like magic!
First, there's the Identity Provider (IdP) – think of it as the playground monitor who knows everyone's name.
Then there's the Service Provider (SP), like your favorite apps and games.
Finally, we've special rules called protocols that help them talk to each other. The system uses password synchronization to keep all your login details matching across different places.
Want to see how they work together? Here's what happens:
- You click to open an app – just like knocking on a friend's door
- The app sends you to the IdP – like asking "Hey, do you know this person?"
- You prove who you're – maybe with a password or fingerprint
- The IdP gives you a special ticket – like a hall pass that lets you into all your apps!
Isn't it cool how they all work together?
Security Advantages and Risk Management
When it comes to keeping secrets safe, having one special key is better than carrying around a whole bunch!
Think of SSO like having a magic key that opens all your favorite toy boxes at once – isn't that neat?
Just like how your parents keep the cookie jar up high to keep it safe, SSO helps protect your online stuff too. This centralized access to multiple applications makes it easier to manage your logins.
It's like having one super-strong password instead of trying to remember lots of different ones. Plus, I've added some extra safety tricks, like asking for a special fingerprint or secret code (that's called multi-factor authentication)!
Want to know the coolest part? SSO watches out for bad guys trying to trick you, just like how your crossing guard keeps you safe at school.
It's always on the lookout, making sure only the right people get in!
If something goes wrong with SSO, you might have trouble getting into your websites since all systems connect through one service.
SSO Authentication Flow and Process
Let's explore how SSO works – it's like playing a game of "Mother May I?" but with computers!
When you want to use an app or website, SSO helps you get in with just one password instead of many. Think of it as having a special key that opens all your favorite doors! This helps prevent password fatigue in users and enhances user convenience across platforms.
The process works like a fun relay race where information passes between different computer friends.
- You knock on the door (website) and say "I want to come in!"
- The door guard (Service Provider) sends you to the password keeper (Identity Provider)
- You show your special badge (password) to the keeper
- The keeper gives you a magic ticket that lets you into all your favorite places
Cool, right? Now you can visit all your favorite spots without stopping to show your badge again!
Essential Components of SSO Systems
Building a Single Sign-On system is like putting together a super-cool team of computer helpers! Let me tell you about the awesome players on this team.
First, we've got the Identity Provider – think of it as a friendly security guard who remembers everyone's secret passwords.
Then there's the Service Provider, like a doorman who checks your special ticket to let you into different apps.
Have you ever played "Simon Says"? Well, Authentication Protocols are like the rules of that game – they make sure everyone's following the same steps to stay safe! Popular options like SAML 2.0 and OIDC help everything work smoothly.
Finally, there's the SSO Architecture, which is like a blueprint for building the perfect digital treehouse. It shows us exactly how to connect all these pieces so you can visit your favorite websites with just one password!
Best Practices for SSO Deployment
Setting up SSO is like building your ultimate playground fort – you've gotta have a super-smart plan!
Think of it as creating a secret clubhouse where only your trusted friends can enter with one special password. I'll show you how to make it awesome and safe!
Here are my top tips for building the perfect SSO fort:
- Start small – test with a tiny group first, just like sharing your new game with your best friend.
- Watch carefully – keep an eye out for any sneaky problems, like a game of hide-and-seek.
- Write everything down – it's like making instructions for your favorite recipe.
- Train everyone – teach your friends the new rules, just like explaining how to play hopscotch.
Using centralized authentication helps keep all your digital spaces safe and sound.
Remember to check your fort regularly to make sure it's strong and secure!
Common Use Cases and Applications
When you look at all the cool ways people use SSO, it's like having a magic key that opens many doors! Imagine if you could use one special password to get into all your favorite games – that's what employees do with enterprise SSO at work. Cool, right?
I love how SSO helps different companies work together too! It's like when you and your friends share playground equipment – everyone gets to play nicely together. Companies can safely share their digital toys (we call them resources) with partner companies. Using token-based mechanisms, SSO keeps data transfers secure between companies.
Have you ever forgotten a password? With SSO, you only need to remember one! Plus, it keeps everything super safe, like having the world's best guard dog watching over your digital stuff.
From schools to stores to big companies, SSO makes logging in fun and easy!
Choosing the Right SSO Solution
Have you ever tried picking your favorite ice cream flavor when there are too many choices? That's exactly what it's like choosing the right SSO solution!
I'll help you pick the perfect one for your needs, just like I'd help you choose between chocolate and strawberry ice cream.
When picking an SSO solution, here's what I look for:
- Does it play nicely with all your apps, like puzzle pieces fitting together?
- Can it protect your passwords like a superhero guards a city?
- Is it easy to use, like riding your favorite bike?
- Will it grow with you, like those cool shoes with room for your toes?
You'll want something that's both strong and simple – kind of like how a turtle's shell is tough but easy to understand!
Modern SSO solutions need to support open standards like SAML for secure data exchange between systems.
Frequently Asked Questions
What Happens to SSO Access When the Internet Connection Is Lost?
When you lose internet, your SSO login might stop working – just like when your favorite video game goes offline!
I'll tell you what happens: you might get kicked out of some apps, while others let you stay logged in for a while using something called a "cached token" (it's like a special pass).
Once you're back online, you'll probably need to log in again to make sure it's really you!
Can SSO Work With Legacy Systems That Don't Support Modern Authentication Protocols?
Yes, I can help SSO work with older systems, even if they're a bit behind the times!
Think of it like using a special translator – we add a bridge program that helps the old system talk to the new SSO.
I'll often use tools called "middleware" or "identity providers" that act like friendly interpreters between the old and new systems, making sure everyone can communicate smoothly.
How Long Do SSO Sessions Typically Last Before Requiring Re-Authentication?
I'll tell you a secret about SSO sessions – they're like timers on your favorite game!
Most SSO sessions last between 1-12 hours before you need to log in again. Some services, like Retool, give you a whole week!
Think of it like a hall pass – you get to move around for a while, but eventually you'll need a new one.
It's all about keeping your info safe and sound!
What Happens if the Identity Provider (Idp) Experiences an Outage?
When an identity provider goes down, it's like when your house key stops working – you can't get in!
I know it's frustrating, but all your apps will be locked until the provider is back up.
Think of it as a chain reaction: one broken link affects everything!
That's why smart companies have backup plans, just like keeping a spare key at your neighbor's house.
Can Users Still Log in Directly to Applications if SSO Fails?
Yes, you can still log in directly to your apps if SSO stops working!
It's like having a backup key when you can't use your main door.
I'll tell you a secret – many apps let you save a special password just for these moments.
Think of it as keeping a spare snack in your backpack when the cafeteria is closed.
You'll still get in, just differently!
The Bottom Line
While Single Sign-On (SSO) simplifies the login process, it's essential to remember that password security is still a critical aspect of online safety. With many applications relying on passwords, managing them effectively is vital to protect your personal information. This is where password management and passkey management come into play. By utilizing robust password management tools, you can ensure that your passwords are secure, unique, and easily accessible, without the hassle of remembering each one.
Don't leave your online security to chance! Take control of your passwords today. Sign up for a free account at LogMeOnce to experience a comprehensive solution that not only manages your passwords but also enhances your overall security. With advanced features and user-friendly interfaces, you can navigate the digital world confidently and securely. Start your journey toward better password management now!

Mark, armed with a Bachelor’s degree in Computer Science, is a dynamic force in our digital marketing team. His profound understanding of technology, combined with his expertise in various facets of digital marketing, writing skills makes him a unique and valuable asset in the ever-evolving digital landscape.





 Password Manager
Password Manager
 Identity Theft Protection
Identity Theft Protection

 Team / Business
Team / Business
 Enterprise
Enterprise
 MSP
MSP