Role of Multi-Factor Authentication Explained

A staggering over 99.99% of Microsoft accounts protected by multi-factor authentication stay secure, even when passwords are leaked. With hackers growing smarter every year, a single password no longer stands a chance. Multi-factor authentication puts more barriers between your accounts and cybercriminals. Whether you manage sensitive business data or personal online profiles, knowing how MFA works and what makes it so effective can help you protect what matters most.
Key Takeaways
| Point | Details |
|---|---|
| Robust Defense | Multi-factor authentication (MFA) requires multiple verification methods, significantly enhancing security against unauthorized access. |
| Variety of Factors | MFA employs three core authentication methods: knowledge, possession, and inherence, each adding unique layers of security. |
| Adaptability | MFA systems adapt to user behavior and context, creating a dynamic security environment that challenges potential intruders. |
| Best Practices | Implementing MFA universally and prioritizing phishing-resistant methods strengthens defenses and reduces vulnerability risks. |
Defining Multi-Factor Authentication and Its Significance
In the digital security landscape, multi-factor authentication (MFA) represents a robust defense mechanism against unauthorized access. According to Wikipedia, MFA is an electronic authentication method that requires two or more distinct types of verification evidence before granting system access. Think of it like a bank vault with multiple locks – each additional factor makes unauthorized entry exponentially more challenging.
The core strength of MFA lies in its layered security approach. Unlike traditional single-password systems, MFA demands users provide multiple proof points such as:
- Something you know (password)
- Something you have (smartphone or security token)
- Something you are (biometric data like fingerprint)
A groundbreaking study analyzing Microsoft Azure Active Directory users revealed extraordinary protection capabilities. Research from the academic paper demonstrated that MFA implementation kept over 99.99% of enabled accounts secure, dramatically reducing compromise risks by more than 99% – even in scenarios where initial credentials were leaked.
By introducing multiple verification layers, MFA transforms digital authentication from a single checkpoint into a comprehensive security ecosystem. It’s not just about preventing unauthorized access; it’s about creating an adaptive, intelligent defense mechanism that evolves with emerging cyber threats. For individuals and organizations alike, MFA represents a critical investment in digital safety, turning potential vulnerabilities into resilient security frameworks.
Types of MFA Methods and Authentication Factors
Multi-factor authentication leverages diverse verification methods to create robust security barriers. According to Coursera, MFA fundamentally relies on three primary authentication factor categories that work together to protect digital identities.
Authentication Factor Categories
The three core authentication factor types include:
- Knowledge Factors (Something You Know)
- Passwords
- Personal identification numbers (PINs)
- Security questions
- Memorable phrases
- Possession Factors (Something You Have)
- Authenticator app codes
- SMS verification codes
- Hardware security keys
- Mobile device authentication
- Inherence Factors (Something You Are)
- Fingerprint scans
- Facial recognition
- Voice recognition
- Retinal eye scans
According to Global Tech Council, these methods provide increasingly sophisticated ways to verify a user’s identity. Each factor adds a unique layer of security, making unauthorized access dramatically more difficult.
While no single method is perfect, combining these authentication factors creates a powerful defense mechanism. Imagine a digital security system where an intruder would need to simultaneously crack your password, possess your physical device, and replicate your unique biometric signature.
 The complexity becomes a powerful deterrent against potential breaches.
The complexity becomes a powerful deterrent against potential breaches.
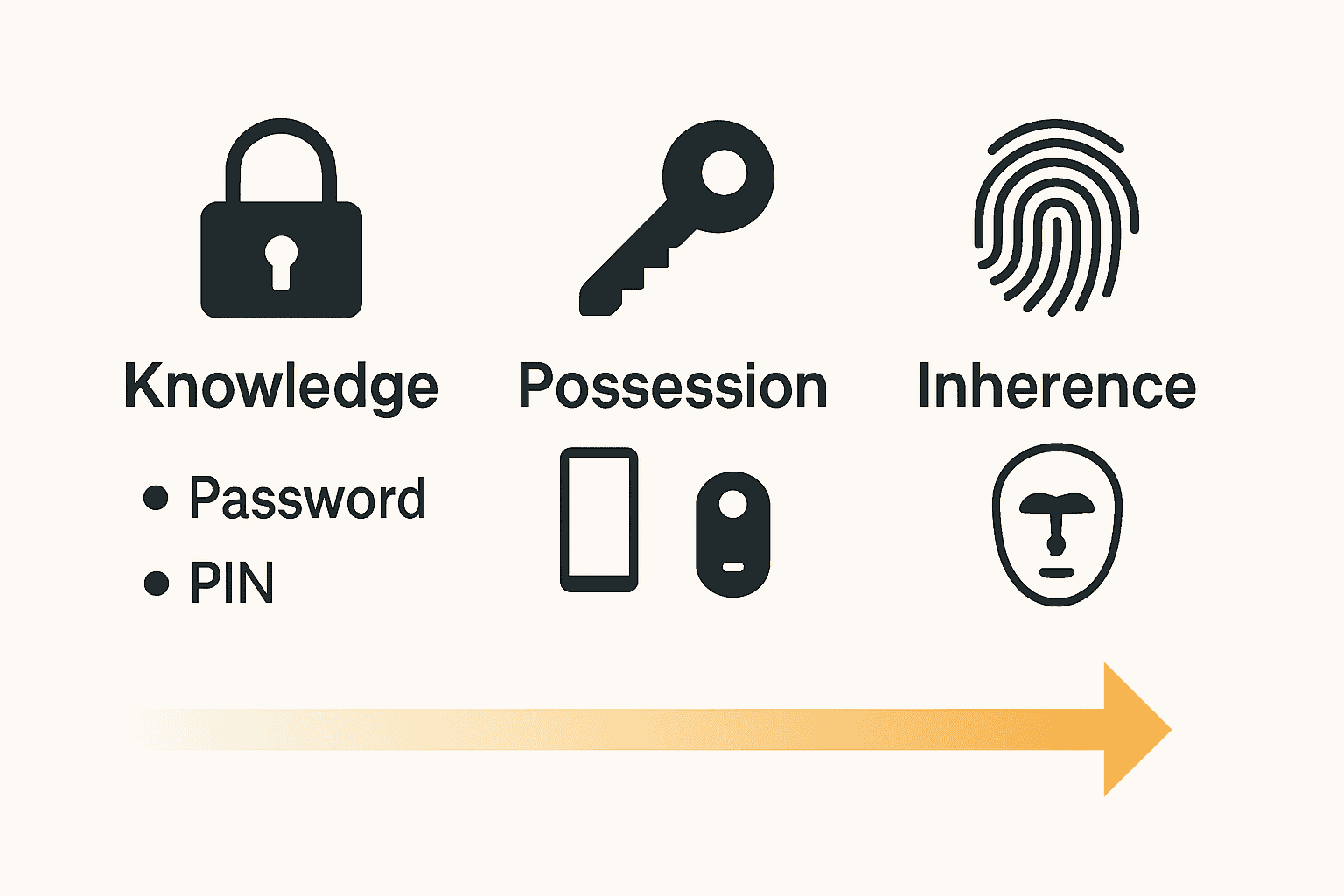
Here’s a comparison of the main MFA authentication factor types:
| Factor Type | Example Methods | Security Strength |
|---|---|---|
| Knowledge (Something You Know) | Password PIN Security question |
Moderate Vulnerable to phishing |
| Possession (Something You Have) | Authenticator app SMS code Hardware key |
High Can resist remote attacks |
| Inherence (Something You Are) | Fingerprint Face scan Voice recognition |
Very High Difficult to replicate |
How MFA Works in Digital Security Systems
Multi-factor authentication operates like a sophisticated digital gatekeeper, creating multiple checkpoints to verify user identity. According to Coursera, the core mechanism involves requiring at least two different verification types before granting system access. Picture it like a security checkpoint where showing one form of identification isn’t enough – you need multiple credentials to proceed.
The Authentication Process
Here’s a typical MFA authentication workflow:
- Enter primary credential (password)
- Trigger secondary verification method
- Complete additional authentication factor
- Gain system access
For example, a user might:
- Enter their standard password
- Receive a time-limited code on their smartphone
- Input that code to complete login
CRITICAL SECURITY INSIGHT: ISACA emphasizes that MFA’s strength lies in creating multiple barriers. Even if a password is compromised, an attacker still needs additional verification – dramatically reducing unauthorized access risks.
The genius of MFA is its adaptability. By requiring verification through different channels – something you know, something you have, something you are – it creates a dynamic security environment that’s continuously challenging for potential intruders. Think of it like a multilayered defense system where each layer makes penetration exponentially more difficult.
Common Challenges and Risks With MFA ImplementationMulti-factor authentication isn’t an impenetrable fortress – it has its own set of complex vulnerabilities. According to Webasha, several sophisticated attack methods can potentially compromise even well-implemented MFA systems.
Primary MFA Vulnerability Vectors
The most significant threats include:
- Phishing Kits: Advanced tools that capture credentials and MFA tokens in real-time
- Adversary-in-the-Middle Attacks: Intercepting communication between authentication systems
- MFA Fatigue Attacks: Continuously spamming push authentication requests
- SIM Swapping: Illegally transferring a user’s phone number to attacker’s device
- Session Hijacking: Bypassing MFA through unauthorized session access
Wikipedia highlights additional implementation challenges beyond direct security risks. Organizations frequently encounter practical obstacles such as:
- High deployment costs
- Complex user hardware token management
- Increased technical support requirements
- User experience friction
While MFA significantly reduces compromise risks, it’s not a silver bullet. The most effective approach involves continuous monitoring, user education, and implementing adaptive authentication strategies that can dynamically respond to emerging threat landscapes. Think of MFA as a robust security layer – strong, but not unbreakable – requiring constant vigilance and strategic refinement.
Best Practices for Secure and Effective MFA Use
Multi-factor authentication requires strategic implementation to maximize its protective potential. According to Tech Bullion, organizations must approach MFA with a comprehensive, adaptive strategy that balances robust security with user experience.
Core MFA Implementation Strategies
Key best practices include:
- Universal Enforcement
- Apply MFA across ALL user accounts and systems
- No exceptions, regardless of user role or access level
- Phishing-Resistant Methods
- Prioritize FIDO2 security keys
- Use authenticator apps over SMS codes
- Implement biometric verification when possible
- Context-Aware Authentication
- Enable adaptive MFA that responds to:
- User location
- Device type
- Network environment
- Historical login patterns
Cloud Security Alliance emphasizes the importance of centralized management. By integrating MFA policies across applications and using standardized protocols, organizations can create a unified, streamlined authentication ecosystem that reduces complexity and potential security gaps.
Ultimately, successful MFA isn’t just about adding layers – it’s about creating an intelligent, flexible system that protects without becoming a barrier to productivity. Think of it as a smart security guard who knows exactly when to be strict and when to allow smooth passage.
Turn Multi-Factor Authentication Knowledge Into Action With LogMeOnce
Reading about the power of multi-factor authentication highlights just how critical layered security is. You now know that traditional passwords are not enough and that real-world risks like phishing, SIM swapping, and MFA fatigue attacks leave sensitive data exposed. If you want to stop worrying about evolving cyber threats and confusing authentication processes, LogMeOnce is here to help.
Discover how easy it is to take back control of your digital identity with LogMeOnce’s passwordless MFA, secure single sign-on, and encrypted cloud protection. Our platform is built for everyone from individual users to large enterprises and government agencies. Get started today with a free trial and see why industry leaders trust our advanced multi-factor authentication and identity management tools. Now is the best time to upgrade your security and outsmart attackers before the next threat hits.
Frequently Asked Questions
What is multi-factor authentication (MFA)?
Multi-factor authentication (MFA) is a security mechanism that requires two or more distinct verification methods to gain access to a system, enhancing digital security beyond just passwords.
What are the common types of authentication factors used in MFA?
MFA typically utilizes three core authentication factors: knowledge factors (e.g., passwords, PINs), possession factors (e.g., mobile devices, security tokens), and inherence factors (e.g., biometric data like fingerprints).
How does MFA work in protecting user accounts?
MFA works by requiring users to provide multiple forms of verification before accessing an account. This layered approach makes it significantly harder for unauthorized users to gain access even if one credential, like a password, is compromised.
What challenges can arise when implementing MFA?
Challenges in MFA implementation can include high deployment costs, complex management of hardware tokens, user experience friction, and potential vulnerabilities against sophisticated cyber attacks such as phishing and session hijacking.

Mark, armed with a Bachelor’s degree in Computer Science, is a dynamic force in our digital marketing team. His profound understanding of technology, combined with his expertise in various facets of digital marketing, writing skills makes him a unique and valuable asset in the ever-evolving digital landscape.





 Password Manager
Password Manager
 Identity Theft Protection
Identity Theft Protection

 Team / Business
Team / Business
 Enterprise
Enterprise
 MSP
MSP



