Password management sounds tedious, but it is the backbone of digital security for billions of users worldwide. You might guess protecting a few passwords is enough, yet over 80 percent of hacking-related breaches involve weak or stolen credentials. The real shock is that even the most high-tech companies can get caught off guard unless they treat password management as a full-scale defense operation.
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement strong, unique passwords for each account | Using varied passwords reduces the risk of unauthorized access across multiple platforms or services. |
| Utilize password management systems for security | These systems securely store, generate, and manage credentials, providing better protection against cyber threats. |
| Avoid sharing login credentials | Sharing passwords increases vulnerability to security breaches and unauthorized access to your accounts. |
| Regularly update your passwords | Frequent password changes help maintain security and mitigate risks associated with credential compromise. |
| Adopt multi-factor authentication | This adds an additional layer of security, making it more difficult for attackers to gain access to your accounts. |
Defining Password Management: Concepts and Importance
Password management represents a critical digital security strategy designed to protect sensitive information across multiple platforms and accounts. At its core, password management involves systematically creating, storing, tracking, and protecting login credentials to ensure robust digital security.
The Core Concept of Password Management
Password management goes beyond simply remembering login details. It encompasses a comprehensive approach to handling authentication credentials that safeguards personal and professional digital identities. Cybersecurity experts from NIST emphasize that effective password management involves several critical components:
- Creating strong, unique passwords for each account
- Securely storing credentials without exposing them to potential breaches
- Implementing regular password rotation and complexity strategies
- Monitoring and detecting potential unauthorized access attempts
The fundamental goal of password management is to reduce the risk of unauthorized system access while maintaining user convenience. By centralizing and securing login credentials, individuals and organizations can significantly minimize the potential for digital security incidents.
Why Password Management Matters in Digital Security
Research from Verizon’s Data Breach Investigations Report consistently highlights that weak or compromised credentials remain a primary vector for cybersecurity attacks. Password management serves as a critical defense mechanism against various digital threats such as:
- Credential stuffing attacks
- Brute force password guessing
- Phishing attempts
- Unauthorized account access
Modern password management solutions provide advanced features like multi factor authentication, encryption, and centralized credential tracking. These tools transform password handling from a manual, error prone process into a systematic, secure approach that protects digital identities across personal and professional domains.
By understanding and implementing robust password management practices, users can create a strong first line of defense against potential cybersecurity threats, ensuring that their digital footprint remains protected and secure.
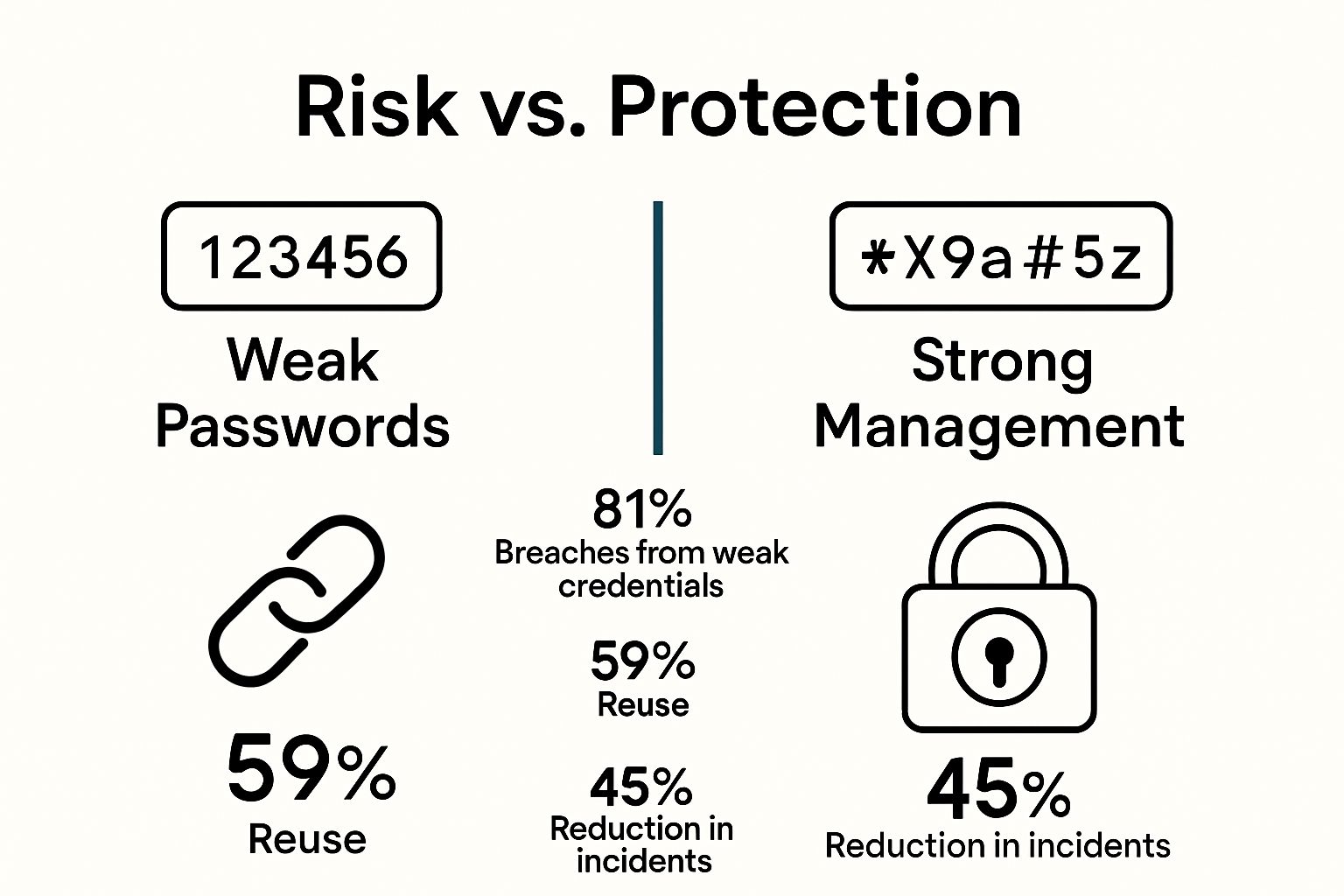
The Risks of Poor Password Practices and Their Implications
Poor password practices expose individuals and organizations to substantial digital security vulnerabilities that can result in devastating consequences. Understanding these risks is crucial for developing robust cybersecurity strategies that protect sensitive information from potential breaches.
Common Password Vulnerability Patterns
Research from IBM’s Security Intelligence reveals that human behavior remains the most significant weakness in digital security infrastructure. Individuals consistently make predictable mistakes that create exploitable entry points for cybercriminals. These vulnerability patterns include:
- Using simple, easily guessable passwords
- Reusing passwords across multiple platforms
- Storing passwords in unsecured digital or physical locations
- Sharing login credentials with unauthorized individuals
- Failing to update passwords regularly
These seemingly minor lapses can provide attackers with comprehensive access to personal and professional digital ecosystems, potentially compromising entire networks of information.
The table below summarizes common password vulnerability patterns and their potential impacts, highlighting why strong password practices are essential for securing digital identities.
| Vulnerability Pattern | Description | Potential Impact |
|---|---|---|
| Simple, guessable passwords | Use of easy words, names, or sequences | Easy for attackers to break into accounts |
| Password reuse across platforms | Same password used on multiple accounts | Increases risk of widespread compromise |
| Unsecured storage of credentials | Saving passwords in unprotected files/locations | Exposes passwords to theft and unauthorized use |
| Sharing login credentials | Giving passwords to others | Higher chance of breaches and unauthorized access |
| Failure to update passwords regularly | Rarely or never changing passwords | Prolongs risk from exposed or stolen credentials |
Financial and Personal Impact of Credential Compromise
Password breaches extend far beyond initial unauthorized access. The Ponemon Institute’s Cost of a Data Breach Report demonstrates that credential-related security incidents can generate substantial financial and reputational damage. Potential consequences include:
- Direct financial losses through unauthorized transactions
- Identity theft and personal information exposure
- Professional reputation damage
- Potential legal and compliance penalties
- Long term credit and financial credibility challenges
Cybercriminals exploit weak password practices through sophisticated techniques like credential stuffing, where stolen login information from one platform is systematically tested across multiple services. This approach amplifies the potential damage of a single compromised password.
By recognizing and addressing these risks, individuals and organizations can implement proactive password management strategies that significantly reduce their vulnerability to digital security threats. Comprehensive protection requires understanding potential weaknesses and developing systematic approaches to credential security.
How Password Management Systems Work: A Detailed Look
Password management systems represent sophisticated digital security solutions designed to streamline and enhance credential protection across multiple platforms and devices. These advanced systems integrate complex technological mechanisms to secure, generate, and manage login credentials with unprecedented efficiency.
Core Technological Architecture
The National Institute of Standards and Technology (NIST) explains that password management systems operate through intricate technological frameworks that prioritize security and user accessibility. The fundamental architecture involves several critical components:
- Secure encrypted storage mechanisms
- Advanced password generation algorithms
- Multi factor authentication integration
- Cross platform synchronization capabilities
- Real time threat detection systems
These systems transform password management from a manual, error prone process into an automated, intelligent security solution that adapts to emerging digital threats. The underlying technology ensures that each credential is uniquely generated, securely stored, and protected against potential unauthorized access.
Authentication and Encryption Mechanisms
Password management systems employ sophisticated encryption protocols that protect user credentials through multiple layers of security. The process involves creating complex cryptographic barriers that prevent unauthorized system entry. Key authentication strategies include:
- Zero knowledge proof authentication
- Biometric verification techniques
- Hardware security key integration
- Advanced encryption standard (AES) protocols
- Continuous credential monitoring
By implementing these advanced security mechanisms, password management systems create a robust digital defense that goes far beyond traditional password protection methods. The technology dynamically adjusts to potential security vulnerabilities, providing real time protection against evolving cyber threats.
The evolution of password management systems represents a critical advancement in digital security, transforming how individuals and organizations protect their most sensitive digital identities. These intelligent systems offer comprehensive protection by combining cutting edge technological innovation with user friendly interfaces that simplify complex security protocols.
Key Features of Effective Password Management Solutions
Effective password management solutions transcend basic credential storage, offering comprehensive digital security ecosystems designed to protect user identities across multiple platforms and environments. These sophisticated systems integrate advanced technological features that provide robust protection against evolving cybersecurity threats.
Core Security Components
Cybersecurity experts from SANS Institute emphasize that robust password management solutions must incorporate multidimensional security strategies. The most critical security components include:
- Advanced encryption protocols
- Comprehensive threat monitoring systems
- Intelligent risk assessment algorithms
- Seamless multi factor authentication
- Dynamic credential rotation mechanisms
These integrated features work synergistically to create a proactive defense mechanism that adapts to emerging digital security challenges. By implementing intelligent security frameworks, password management solutions transform traditional credential protection into a dynamic, responsive system.
User Experience and Accessibility Features
Password management solutions balance stringent security requirements with user friendly interfaces that simplify complex authentication processes. Modern solutions recognize that optimal security cannot compromise user accessibility. Key accessibility features include:
- Cross platform synchronization
- Intuitive credential generation interfaces
- Secure password sharing capabilities
The most sophisticated password management systems provide seamless integration across devices and platforms, enabling users to maintain robust security without experiencing friction in their digital interactions.
This table provides an overview of core security and user experience features found in effective password management solutions, allowing readers to quickly compare their benefits and roles.
| Feature Category | Key Feature | Benefit |
|---|---|---|
| Security | Advanced encryption protocols | Protect stored credentials from unauthorized access |
| Security | Comprehensive threat monitoring | Detects and responds to suspicious activity in real time |
| Security | Intelligent risk assessment | Analyzes threats and adapts protection measures dynamically |
| Security | Multi-factor authentication | Adds an additional security layer beyond just passwords |
| User Experience | Cross-platform synchronization | Enables seamless use across devices and systems |
| User Experience | Intuitive credential generation | Makes creating strong, unique passwords quick and easy |
| User Experience | Secure password sharing | Allows authorized sharing without compromising security |
| This approach ensures that security protocols enhance rather than obstruct user experience. |
By combining advanced technological capabilities with user centric design, password management solutions provide a comprehensive approach to digital identity protection. These systems represent more than simple tools they are intelligent security ecosystems that adapt to the complex and constantly evolving digital landscape.
Real-World Applications of Password Management in Various Sectors
Password management solutions have become critical infrastructure across diverse professional and organizational environments, providing tailored security strategies that address unique digital protection challenges. These sophisticated systems adapt to specific sector requirements, ensuring comprehensive credential protection and risk mitigation.
Enterprise and Corporate Security Implementations
Gartner Research demonstrates that enterprise password management goes far beyond traditional security protocols. Corporate implementations focus on creating centralized, controlled credential ecosystems that protect sensitive organizational data. Critical enterprise applications include:
- Centralized credential tracking for large workforce environments
- Comprehensive access control management
- Automated compliance and security reporting
- Integration with existing organizational IT infrastructure
- Role based credential access permissions
These enterprise solutions transform password management from an individual security practice into a strategic organizational defense mechanism that minimizes potential security vulnerabilities and maintains strict access control standards.
Sector Specific Password Management Strategies
Different industry sectors require nuanced password management approaches that address their specific regulatory and operational requirements. Financial institutions, healthcare organizations, and government agencies develop specialized password management solutions tailored to their unique security landscapes:
- Financial sector: Enhanced transaction authentication protocols
- Healthcare: HIPAA compliant credential management systems
- Government: Multilayered security clearance credential tracking
- Educational institutions: Student and faculty credential segregation
- Technology companies: Advanced multi factor authentication frameworks
By implementing sector specific password management strategies, organizations can develop robust security ecosystems that protect sensitive information while maintaining operational efficiency. These targeted approaches recognize that digital security is not a one size fits all solution but a dynamic, context specific challenge that requires sophisticated, adaptive technologies.

Ready to End Password Risks? Discover How LogMeOnce Transforms Your Security
Are you worried about weak passwords, password reuse, or the constant threat of unauthorized access? This article has shown how poor password habits and outdated tools can put your financial and personal data at serious risk. If you want to defeat credential stuffing, prevent data breaches, and keep your organization secure, you need more than just advice. You need a full-featured password management solution that combines encrypted storage, single sign-on, and real-time threat monitoring—just like the systems described above.
Stop letting manual errors and overlooked risks hold you back. Visit LogMeOnce Resources to see how our solutions simplify strong password management, offer powerful passwordless MFA, and give you dark web monitoring at your fingertips. Discover clear comparisons, free trials, and proven security features that protect personal users, businesses, and government organizations. Take the first step to digital peace of mind and upgrade your security posture now. Explore LogMeOnce today to learn more and stay ahead of tomorrow’s threats.
Frequently Asked Questions
What is password management?
Password management is a digital security strategy that involves creating, storing, and protecting login credentials for various accounts. To implement effective password management, use a password manager to generate unique, strong passwords for each account.
Why is password management important for digital security?
Password management is crucial because it defends against unauthorized access, credential stuffing, and phishing attacks. Start using a password management solution to enhance your security and reduce the risk of data breaches.
How can I create strong passwords for effective password management?
To create strong passwords, use a mix of uppercase and lowercase letters, numbers, and special characters, and avoid using easily guessable information. Aim for passwords that are at least 12 characters long to maximize security.
How often should I update my passwords for effective management?
It’s recommended to update your passwords every 3 to 6 months to maintain security. Create a reminder to review and update your passwords regularly, ideally at the beginning of each season.
What features should I look for in a password management solution?
Look for features such as encryption, multi-factor authentication, and cross-platform synchronization in a password management solution. Prioritize systems that offer real-time threat detection to further enhance your security.
How can password management benefit both individuals and organizations?
Password management benefits individuals and organizations by protecting sensitive information and reducing the risk of data breaches. Implement centralized password management in your organization to improve access control and compliance with security standards.

Mark, armed with a Bachelor’s degree in Computer Science, is a dynamic force in our digital marketing team. His profound understanding of technology, combined with his expertise in various facets of digital marketing, writing skills makes him a unique and valuable asset in the ever-evolving digital landscape.





 Password Manager
Password Manager
 Identity Theft Protection
Identity Theft Protection

 Team / Business
Team / Business
 Enterprise
Enterprise
 MSP
MSP



