Passwords feel like tiny locks on our biggest secrets, from banking info to work emails. Yet over 80 percent of hacking-related breaches start with stolen or compromised passwords. Most people think their old login is safe as long as they never share it. The real danger is that stale passwords quietly become open doors for cybercriminals, and you never see it coming until it is too late.
Quick Summary
| Takeaway | Explanation |
|---|---|
| Regularly update passwords frequently. | Stale passwords increase vulnerability and risk of cyberattacks. Change them often to enhance security. |
| Use unique passwords for every account. | Reusing passwords heightens the risk across multiple platforms. Each account should have a distinct password. |
| Implement multi-factor authentication. | Adding another layer of security protects accounts even if passwords are compromised. Consider it essential for safeguarding sensitive information. |
| Create complex passwords with variety. | Combine letters, numbers, and symbols in passwords to make them harder for cybercriminals to guess or crack. |
| Stay informed about emerging security technologies. | Keeping up with innovations like biometric verification and passwordless systems can improve your security posture against evolving threats. |
The Importance of Strong Passwords in Digital Security
In an increasingly interconnected digital world, passwords serve as the primary gatekeepers protecting our most sensitive personal and professional information. Understanding why update passwords regularly and maintaining robust password security has become paramount in defending against sophisticated cyber threats.
The Foundation of Digital Defense
Passwords act as the first line of defense against unauthorized access to personal accounts, financial systems, professional networks, and critical infrastructure. The UK National Cyber Security Centre emphasizes that weak passwords remain one of the most common vulnerabilities exploited by cybercriminals. Attackers leverage advanced techniques like credential stuffing, password guessing, and brute force attacks to breach digital systems.
Key vulnerabilities that make passwords critical include:
- Protecting personal identity information
- Securing financial transactions and banking credentials
- Preventing unauthorized access to professional communication platforms
- Safeguarding cloud storage and sensitive digital assets
Understanding Password Risks
Cybercriminals have developed sophisticated methods to compromise password security. Dictionary attacks, which systematically attempt common word combinations, and rainbow table attacks that leverage precomputed password hash databases represent significant threats. Modern hackers utilize powerful computational resources and machine learning algorithms to rapidly test millions of potential password combinations.
Statistically, users who reuse passwords across multiple platforms exponentially increase their risk of comprehensive digital compromise. A single weak password can provide attackers with a gateway to multiple personal and professional accounts, potentially resulting in identity theft, financial fraud, and extensive data breaches.
Strategic Password Management
Effective password security requires a comprehensive approach. This includes creating complex, unique passwords for each account, utilizing multi factor authentication, and implementing regular password rotation strategies. Users should prioritize passwords that combine uppercase and lowercase letters, numbers, and special characters while avoiding predictable personal information like birthdays or common names.
By understanding the critical role passwords play in digital security, individuals and organizations can proactively protect their digital identities and maintain robust cyber resilience.
Understanding the Risks of Stale Passwords
Passwords that remain unchanged for extended periods become increasingly vulnerable to sophisticated cyber attacks. Understanding the inherent risks associated with outdated credentials is crucial for maintaining robust digital security and protecting sensitive information from potential breaches.
The Silent Threat of Unchanged Credentials
The U.S. Cybersecurity and Infrastructure Security Agency warns that passwords which are not regularly updated can become significant security liabilities. Stale passwords are particularly dangerous because they accumulate multiple risk factors over time, creating multiple potential entry points for malicious actors. The longer a password remains unchanged, the more opportunities cybercriminals have to compromise digital systems.
Key risks associated with unchanged passwords include:
- Increased exposure from previous data breaches
- Accumulation of potential vulnerabilities
- Higher likelihood of credential discovery through advanced hacking techniques
- Reduced effectiveness of existing security protocols
Mechanisms of Password Vulnerability
Cybercriminals employ advanced techniques to exploit stale passwords. Dark web marketplaces continuously trade stolen credentials, allowing attackers to compile extensive databases of potentially compromised login information. Machine learning algorithms enable rapid testing of password combinations, making it easier to breach accounts with predictable or long-standing credentials.
Statistical evidence demonstrates that passwords unchanged for more than six months are significantly more likely to be successfully compromised.
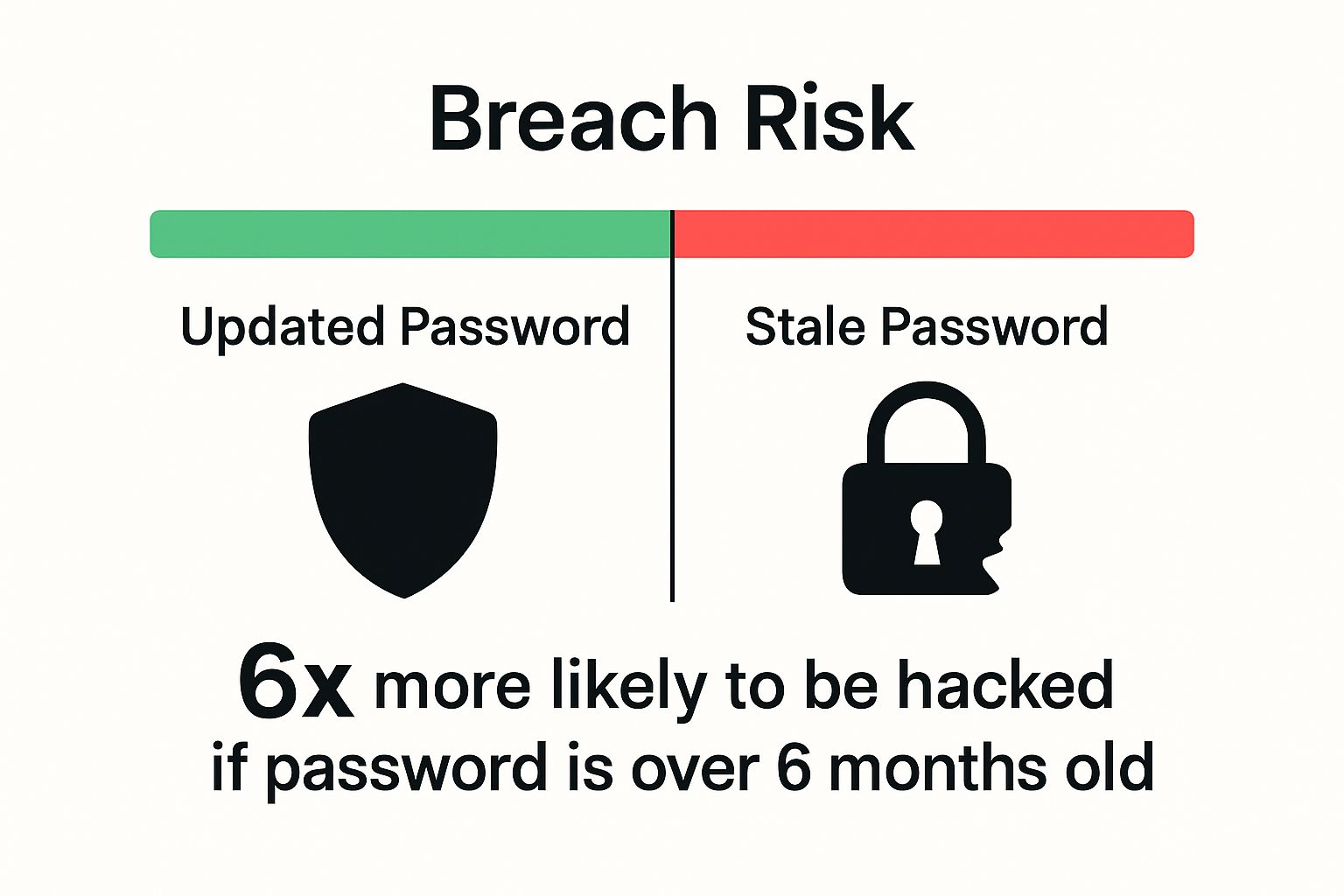 Each passing month increases the probability of unauthorized access, as technological capabilities for breaking encryption continuously improve.
Each passing month increases the probability of unauthorized access, as technological capabilities for breaking encryption continuously improve.
Proactive Password Protection Strategies
Mitigating the risks of stale passwords requires a comprehensive approach to digital security. Organizations and individuals must implement dynamic password management strategies that include regular credential rotation, complex password generation, and continuous monitoring of potential security breaches. Multi-factor authentication provides an additional layer of protection, creating redundant security mechanisms that extend beyond traditional password-based access controls.
By recognizing the dynamic nature of cybersecurity threats, users can develop more resilient approaches to protecting their digital identities and sensitive information.
How Passwords are Compromised and the Impact
Password compromise represents a critical vulnerability in digital security, with far-reaching consequences that extend beyond immediate account access. Understanding the intricate mechanisms cybercriminals employ to breach digital defenses is essential for developing robust protective strategies.
The Anatomy of Password Breaches
Verizon’s Data Breach Investigations Report reveals that over 80% of hacking-related breaches involve stolen or compromised credentials. Attackers utilize sophisticated techniques that exploit human behavior, technological vulnerabilities, and complex digital ecosystems to gain unauthorized access.
Primary methods of password compromise include:
- Social engineering tactics
- Credential stuffing attacks
- Phishing schemes
- Brute force password guessing
- Exploiting software vulnerabilities
Advanced Exploitation Techniques
Cybercriminals have evolved beyond simple guessing techniques, developing complex strategies that leverage advanced computational technologies. Machine learning algorithms enable rapid password cracking, while dark web marketplaces facilitate the trading of stolen credentials. Sophisticated attackers use combination attacks that merge multiple breach methodologies, creating multilayered approaches to password exploitation.
The computational power available to modern hackers allows them to test millions of password combinations within minutes. Graphics processing units and distributed computing networks dramatically accelerate the process of breaking encryption, making even moderately complex passwords vulnerable to systematic attacks.
Comprehensive Impact of Password Breaches
The consequences of password compromise extend far beyond initial unauthorized access. Financial losses, reputational damage, and potential long-term identity theft represent significant risks. Organizations may face regulatory penalties, while individuals could experience devastating personal and professional disruptions.
To help clarify the ways passwords are compromised and their resulting effects, the table below outlines common breach methods alongside their primary impacts.
| Breach Method | Description | Potential Impact |
|---|---|---|
| Social Engineering | Manipulating users into revealing credentials | Unauthorized account access |
| Credential Stuffing | Using stolen data to try multiple accounts | Widespread account compromise |
| Phishing Schemes | Tricking users to give up passwords | Identity theft, data breaches |
| Brute Force Guessing | Systematically testing password combinations | Rapid breakdown of weak passwords |
| Exploiting Software Flaws | Using bugs to access stored credentials | Systemwide data exposure |

By recognizing the sophisticated landscape of digital threats, users can develop more proactive and comprehensive approaches to password security. Understanding these complex compromise mechanisms is the first step toward creating more resilient digital defense strategies.
Best Practices for Password Updates and Management
Password management represents a critical component of comprehensive digital security strategy. Developing robust practices for creating, maintaining, and updating passwords can significantly reduce the risk of unauthorized access and potential data breaches.
Strategic Password Creation Principles
The National Institute of Standards and Technology (NIST) provides comprehensive guidelines for developing secure password strategies. Effective password creation goes beyond simple complexity requirements, focusing on developing unique, memorable, and resilient credential systems that protect against modern hacking techniques.
Key principles for creating strong passwords include:
- Prioritize length over complexity
- Avoid predictable patterns and personal information
- Use unique passwords for each account
- Consider using passphrase approaches
- Implement random character combinations
Advanced Password Protection Techniques
Modern password management requires a multi layered approach that extends beyond traditional password creation methods. Implementing advanced security techniques helps create more robust digital protection mechanisms. Password managers, multi factor authentication, and regular credential rotation serve as critical components of a comprehensive security strategy.
Cybersecurity experts recommend developing a dynamic approach to password management that includes continuous monitoring and proactive security measures. This involves regularly assessing potential vulnerabilities, tracking potential data breaches, and maintaining a flexible approach to credential protection.
Comprehensive Password Management Strategies
Effective password management is an ongoing process that requires consistent attention and strategic thinking. Organizations and individuals must develop holistic approaches that combine technological solutions with user education and awareness. This includes implementing robust password policies, providing security training, and creating systems that support secure credential management.
By adopting a proactive and comprehensive approach to password updates and management, users can significantly reduce their vulnerability to cyber threats and protect their most sensitive digital assets.
The following table summarizes key best practices for creating and managing strong passwords, based strictly on National Institute of Standards and Technology (NIST) guidelines and content from the article.
| Best Practice | Description |
|---|---|
| Prioritize Length over Complexity | Longer passwords offer more protection than just complexity. |
| Avoid Predictable Patterns | Do not use birthdays, names, or common sequences. |
| Unique Passwords for Each Account | Do not reuse passwords across multiple accounts. |
| Use Passphrases | String together unrelated words for strength and memorability. |
| Random Character Combinations | Mix letters, numbers, and symbols for added security. |
The Future of Password Security: Trends and Innovations
The digital security landscape continues to evolve rapidly, with emerging technologies and innovative approaches transforming traditional password protection strategies. Understanding these emerging trends is crucial for anticipating and preparing for the next generation of cybersecurity challenges.
Emerging Authentication Technologies
Gartner Research highlights the growing shift towards advanced authentication methods that move beyond traditional password-based systems. Biometric technologies, artificial intelligence, and adaptive authentication mechanisms are reshaping how digital identities are verified and protected.
Key emerging authentication technologies include:
- Behavioral biometric authentication
- Continuous authentication systems
- Artificial intelligence driven security protocols
- Decentralized identity verification
- Quantum encryption technologies
Passwordless Authentication Strategies
Modern cybersecurity experts are developing innovative approaches that fundamentally challenge traditional password models. Passwordless authentication systems leverage advanced technologies like blockchain, biometric verification, and machine learning to create more secure and user friendly digital access mechanisms. These approaches eliminate the vulnerabilities associated with traditional password storage and transmission.
Advanced authentication methods use complex algorithms that analyze multiple contextual factors, including user behavior, device characteristics, and geographical location. This multilayered approach creates a more dynamic and adaptive security environment that can respond to potential threats in real time.
The Convergence of Security Technologies
The future of digital security lies in integrated, intelligent systems that combine multiple authentication technologies. Organizations are moving towards comprehensive security ecosystems that seamlessly blend artificial intelligence, biometric verification, and advanced encryption technologies. These holistic approaches provide more robust protection while simultaneously improving user experience and accessibility.
As digital technologies continue to advance, password security will increasingly rely on sophisticated, adaptive systems that can anticipate and neutralize emerging cyber threats. Users and organizations must remain flexible and proactive in adopting these cutting edge security innovations.
Bring an End to Password Risks with LogMeOnce
Are you concerned about password breaches or frustrated by the anxiety of not knowing if your credentials are already exposed? The article highlighted how uncontrolled password risks, stale credentials, and weak update habits leave individuals and businesses vulnerable to credential stuffing, data breaches, and future hacking attempts. Waiting too long to update passwords increases the likelihood of falling victim to constantly evolving cyber threats, especially as attackers use more sophisticated tools every day.
LogMeOnce offers you real solutions that take the stress out of password management. With features like automated password rotation, single sign-on, and passwordless multi-factor authentication, we make it simple for you or your organization to keep your digital identity secure. Visit LogMeOnce Resources to see how our platform goes beyond traditional password strategies with encrypted cloud storage and dark web monitoring. Take action today by exploring a free trial, reviewing solution comparisons, and discovering tools that put you in control. Start prioritizing your security with solutions designed for individuals and businesses who refuse to settle for outdated, risky credentials.
Frequently Asked Questions
Why is it important to update passwords regularly?
Regularly updating passwords is crucial because it minimizes the risk of unauthorized access to your accounts. Stale passwords can accumulate vulnerabilities, making them easier targets for cybercriminals.
How often should I change my passwords?
It is recommended to change your passwords at least every six months or sooner if you suspect that any of your accounts may have been compromised.
What are the best practices for creating strong passwords?
Best practices include using a combination of uppercase and lowercase letters, numbers, and special characters. Avoid predictable patterns or personal information, and consider using passphrases for added security.
How can I protect myself against password compromises?
To protect against password compromises, use unique passwords for each account, enable multi-factor authentication, and consider employing a password manager to keep your credentials secure.
Article generated by BabyLoveGrowth

Mark, armed with a Bachelor’s degree in Computer Science, is a dynamic force in our digital marketing team. His profound understanding of technology, combined with his expertise in various facets of digital marketing, writing skills makes him a unique and valuable asset in the ever-evolving digital landscape.





 Password Manager
Password Manager
 Identity Theft Protection
Identity Theft Protection

 Team / Business
Team / Business
 Enterprise
Enterprise
 MSP
MSP



